Source: iranwire.com
Kian Sabeti
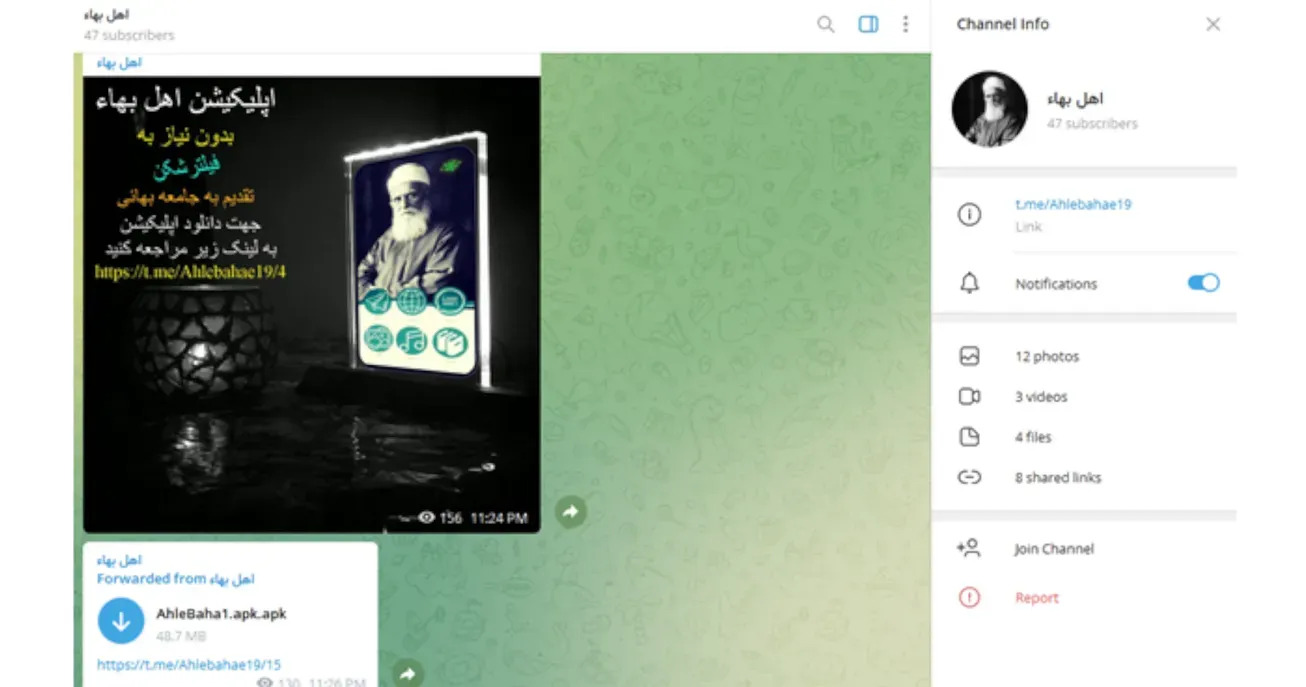
In recent days, internet security experts and members of the Baha’i community have warned that hackers affiliated with the Islamic Republic have been using an app called Ahl-e Baha (“The People of Baha”) to spy on Baha’is and steal their personal information.
The Islamic Republic’s policy towards Iranian Baha’is has, since 1979, been to silence them and to spread disinformation against the community. The authorities have used every communication tool at their disposal, from books and newspapers to audio and visual media, and now online, to unilaterally attack Baha’is for their religious beliefs. For a long time, even the word “Baha’i” was filtered in Google searches.
More recently, whenever a report or a news item about Baha’is appeared on Persian-language websites based outside of Iran, agents of the Iranian government’s digital security forces would post insulting comments under them, using fake names. The latest approach, however, is a little different.
The spyware app Ahl-e Baha purports to be run by Baha’is. It uses a Telegram channel of the same name to encourage Baha’is to download and install the app on their smartphones. But like other malicious apps aimed at the Iranian diaspora, the platform is insecure and allows hackers to gather users’ personal information.
When the experts discovered the nefarious nature of the app they alerted members of the Baha’i community, via Telegram, and warned them to not use it.
Ahl-e Baha’s Telegram channel was launched on February 9, 2022, according to the date of its first post. The channel started by displaying a picture of Abdu’l-Baha, the son of Baha’u’llah, the prophet of the Baha’i faith, who led the Baha’i community from 1892 until 1921. The following postings were then promotions for the Ahl-e Baha app as a service provided by young Baha’is.
Since early March, probably because few Baha’is fell into its trap, the channel started to post Baha’i teachings and prayers even as it continued to promote the app. “Dedicated to the Baha’i Community” and “A Complete Collection for the Needs of the Ahiba” [the beloved (of God), a term that Baha’is use to refer to their coreligionists], are among the mottos they have used for this purpose.
Every image promoting Ahl-e Baha declared that it had “no need for filter-breakers”. This claim, by itself, and in particular because it is stated publicly, raised suspicions. Every app, site and blog related to the Baha’i community and the Baha’i faith is filtered in Iran. If the makers of this app had any connections to the Baha’i community they would have known that this would immediately lead to its filtering.
“The size of the Ahl-e Baha app was unusually big, around 50 to 60 megabytes,” the Baha’i computer expert tells IranWire. “Such a size for an app with this functionality is suspicious. We became more suspicious when we found out that it asks the user for many permissions to access the information provided by and stored on the phone, when an app like this has no need for so many permissions. For example, it wants permission to access location, all contacts, all files, all pictures, text messages, and so on.”
Ahl-e Baha is not abailable on Google Play because Google does not approve apps that ask for excessive permissions. The app can be only downloaded from the Ahl-e Baha Telegram channel and “side-loaded” on to smartphones.
“After the app provoked some suspicion,” the expert went on, “our colleagues in information technology at Iran’s Baha’i Institute for Higher Education [BIHE, an informal or “underground” university that serves Baha’is denied access to public universities] disassembled the app and found that it hides a dangerous backdoor.
“Backdoors provide hackers with a gateway into the operating system and allows them to access the system by bypassing security measures. And since the backdoors are invisible, users might never know that another party has infiltrated the system.
“After we found the backdoor, we traced the IP addresses this app uses and found out that it uses two; one of these gets menu information such as Baha’i teachings, prayers and history, and gives them to the users, while the other IP address gathers information from the phone and stores it somewhere else.
“When we traced the second IP address, we found that the server belonged to a shell company in London. The name of the company was probably taken from a comic strip. When we dug into it even more, we learned the IP address was used in a 2019 cyberattack by a hacker group by the name of Muddy Water, under the direction of Iranian government.
“In the past few days, the location of the server changed. Now it’s registered in the American state of Delaware under another fictitious name.”
On 12 January, 2022, meanwhile, and for the first time, a spokesperson for the United States military’s cyber command explicitly connected Iran’s Intelligence Ministry with the espionage and hacking group known as Muddy Water.
The group has tried to siphon data from telecoms firms and other organizations across the Middle East. Cyber Command published samples of malicious code allegedly used by the Iranian hackers to help organizations in the US and elsewhere defend themselves from future intrusion attempts.
On 24 February, 2022, Reuters reported that according to the US Federal Bureau of Investigation, the Cybersecurity and Infrastructure Security Agency, and British and other US authorities, Muddy Water had targeted a range of government and private-sector organizations in multiple sectors across Asia, Africa, Europe and North America. They said they had observed this malicious actor targeting telecommunications, defense, local government, and the oil and natural gas sectors.
Muddy Water has reportedly been active since November 2019. In October 2021, the cyber security firm IBM X-Force identified Muddy Water as one of three major Iranian state-sponsored cyber security threat actors. The firm said Muddy Water was responsible for attacks targeting Turkey and Persian Gulf countries with the goal of deploying remote access “Trojan horses” inside the compromised systems.
A Trojan horse exploit, much like the Greek myth, inserts malicious code into a system after which it is deployed to take over or damage the system.
The computer expert who spoke with IranWire says the best course of action is to not install Ahl-e Baha. But users who have installed it must be aware that the app also installs an invisible second app. A standard uninstall would remove the first app, he said, but not the second one. Their phone should be reset to factory settings.
Leave a Reply